The Battlefield is Evolving
The Increased Threat of Cyber Attack Affects Strategic Decision Making
As technologies continue to advance and become more deeply ingrained in modern life, threats of a crippling cyber attack or electronic warfare (EW) become increasingly probable. In an attempt to mitigate these risks, the Colombian national government (represented by the Ministry of Information Technology), the Higher War School in Colombia, and ITM Consulting Company joined forces to explore the role simulation plays in understanding, preparing for, and combating cyber attacks.
To build electronic warfare scenarios, the organizations needed a tool that could create and model elements vulnerable to cyber attacks, such as radar systems, military and civilian entities, and communication systems; they chose MAK’s VR-Forces simulation software tool for the job. VR-Forces not only allowed them to create scenarios to play out different threats in different environments but also gave them the freedom to redesign the User Interface (UI) to match specific scenario needs. The group conducted three major cyber attack scenarios, which they are using to create response strategies.
In the first scenario, VR-Forces simulated two aircraft teams, where the red team was given a mission to use scanners and jammers to alter the frequency on the blue team’s radar systems; doing this enabled the red team to use attack aircraft to undermine the blue team’s defense system (see Figure 1).
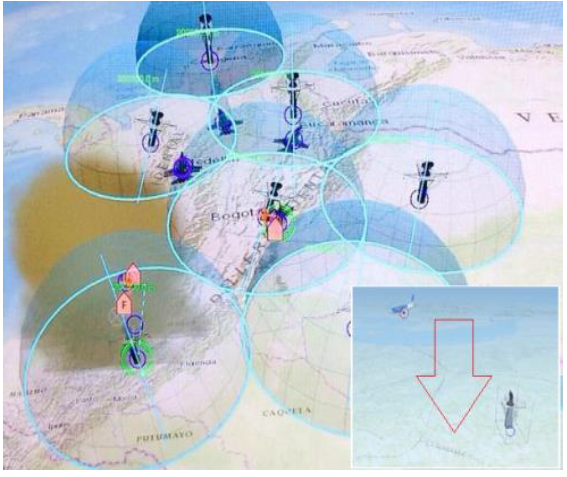
Figure 1: Illustration of a Radar Attack
The second scenario uses VR-Forces to simulate an electronic warfare attack on the Colombian oil infrastructure, a victim of frequent terrorist attacks. In this exercise, the red team was instructed to alter the readings on specific valves on a pipeline to ignite fires. Additionally, attacks on the blue team’s surveillance systems (unmanned aircraft) set out to deter the blue team’s response (see Figure 2).
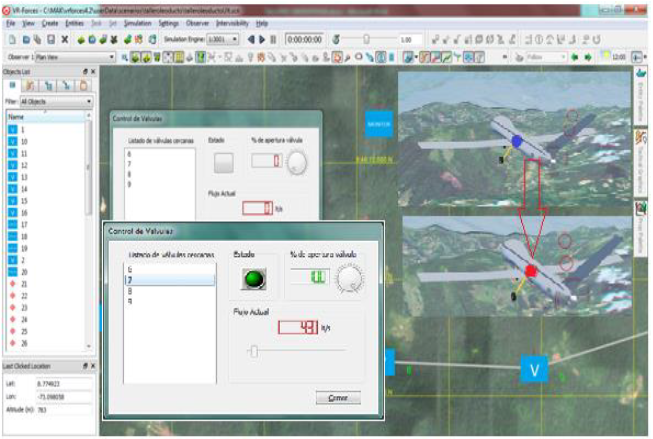
Figure 2: Cyber Attack on a Colombian Oil Infrastructure
A third scenario highlights the danger to the civilian population if the turbines in a hydroelectric plant are compromised through a cyber attack. The red team in this situation instigates drastic variations in water levels at the plant that in turn disrupt the power and energy generated to the nearby town. The power and energy disruptions bring about detrimental consequences for the simulated town (see Figure 3).
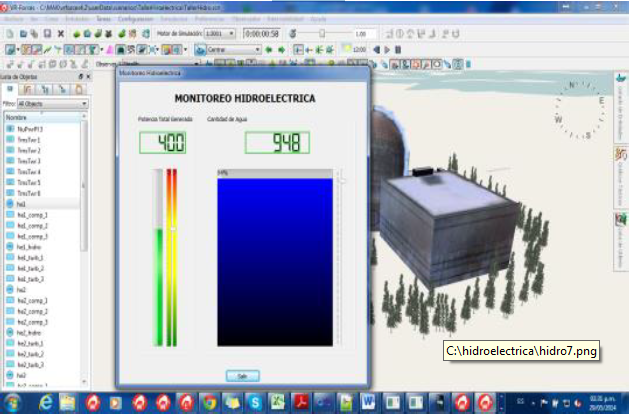
Figure 3: Cyber Attack on the Colombian Critical Infrastructure
The exercises using VR-Forces have contributed to research and development efforts led by the Department of Telematics ESDEGUE, and in particular its line of research in Cybersecurity and Cyber Defense.

